Orginal content provided by BDO Australia
On Friday, the world experienced the wrath of a well-coordinated ransomware attack, known as WannaCry. A number of large companies have already been impacted, including Britain’s public health system, FedEx in the USA and Spanish telecom provider Telefonica.
As of this morning, the Australian Cyber Security Centre indicated that none of the Federal agencies have been attacked, however some private sector organisations experienced attacks.
Don’t assume you are protected against ‘WannaCry’
The malware causing the headache right now is known as ‘WannaCry’. This is one of the largest reported global ransomware attacks, shutting down hospitals and causing havoc for organisation around the world.
WannaCry (also known as WanaCrypt0r 2.0) has a classic ransomware functionality – when a machine (or computer) becomes infected, the files on local disks and network storage are encrypted. Once the files are encrypted, the criminal/s demand a ransom payment in exchange for the recovery of affected the files. The ransom demanded is between US$300 and US$600 – example shown below:
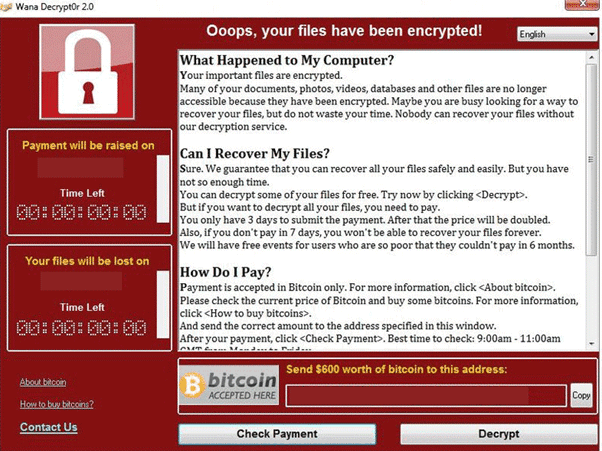
Ransomware attacks are not new! They have been plaguing businesses for years due to its very efficient approach for criminals to extort money.
BDO has outlined why it is a cause for concern and prepared some important measures you can take now to avoid this worldwide cyber threat.
Why you should be concerned
- WannaCry is using self-propagating techniques to spread between machines (this malware is categorised as a worm rather than just a virus). These characteristics mean the code within this piece of malware looks for other machines on the same network as itself to infect. When it finds another machine it copies itself, and the process begins again.
- WannaCry is exploiting a vulnerability within machines which was only recently disclosed which makes many organisations vulnerable to this malware.
- Since Friday 12 May 2017, WannaCry has impacted 170,000+ machines across 100 countries.
- The code within the malware has already been altered by the criminal/s to change the way it works. Which means it can avoid detection by security controls, such as anti-malware and intrusion detection systems being used to stop its spread.
BDO Recommendations
It’s not too late if you haven’t had an attack. You should immediately request your IT team to apply Microsoft's security patches, especially MS17-010. Installation of security patches is extremely important when it comes to defending against cyber-attacks, especially WannaCry.
Important things to consider:
- Enabling strong spam filters to prevent phishing e-mails from reaching the end.
- Request all users to be vigilant about opening attachments and links in e-mails, especially if they don’t recognise the sender or are not expecting the message. If there are any doubts delete the message before opening it.
- Ensure anti-virus and anti-malware solutions are set up to date, and configured to automatically conduct regular scans.
- Disable macro scripts from Microsoft Office files transmitted via e-mail. Consider using Office Viewer software to open Microsoft Office files received via e-mail instead of full Office suite applications.
- Consider taking a back-up of critical data and moving it to off-line storage.
Already attacked? Don’t panic, act now by:
Get a good view of the situation at hand with the following tips, or contact an expert to assist you.
- Isolate computers that have been compromised to ensure they can't spread the malware to other machines. Don’t forget to disconnect the wireless network adapter too!
- Isolate Windows machines of high value, such as file servers, backup or machines that are part of critical processes to ensure they can't be reached by compromised machines.
- Limit access to network storage solutions to prevent compromised machines from encrypting the information.
- Install security patches on all Windows machines that are clean.
- Start recovery and reinstall compromised computers. Remember to apply the security patches before reconnecting to the network!
You need to apply security patches to all Windows computers, not just the ones with Internet access. A fully patched machine in your network can still be infected with WannaCry. Given a malicious email and some user interaction, it can spread the malware to other machines in the network, including machines indirectly exposed. It's not rare for BDO to encounter a practice where security patches are only applied to machines close to the Internet perimeter.